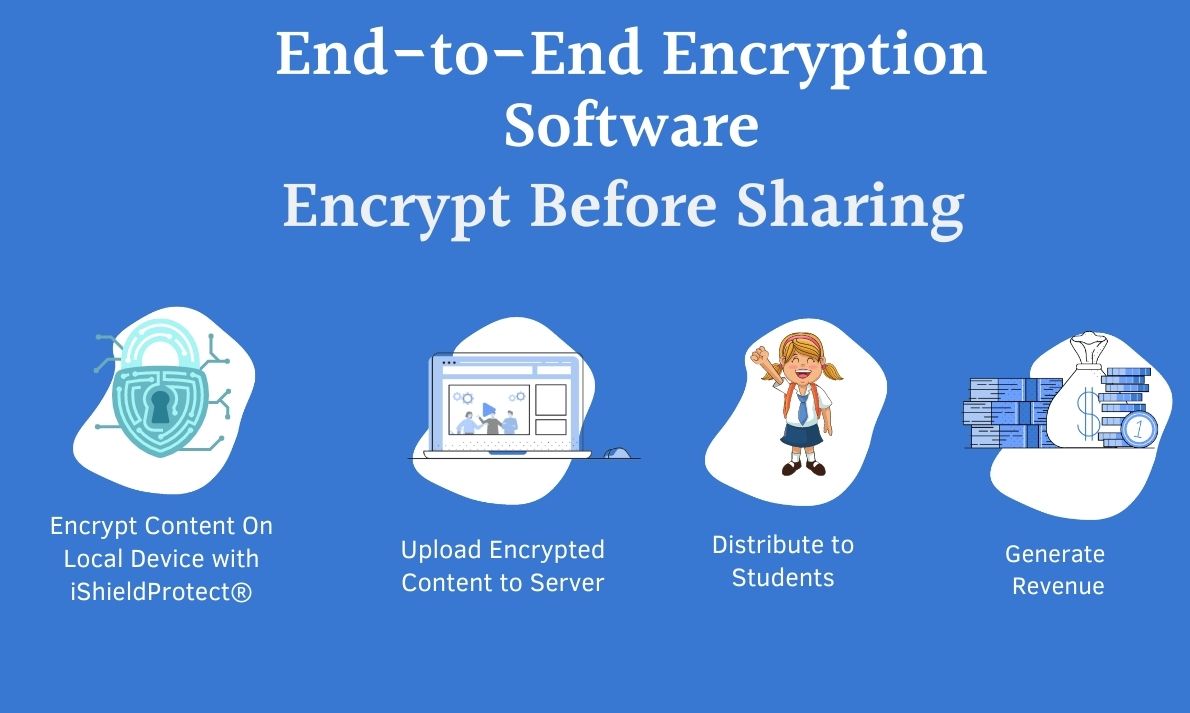
With end-to-end encryption (E2EE), all of your data is encrypted (kept secret) until it reaches its destination. End-to-end encryption protects your data from being seen by any third parties in the middle, whether you are using it for texting, email,…
What is video copy protection software? Video copy protection is a process of protecting premium video content from unauthorized access. This process involves encrypting videos using encoding software & hardware so that no one can access the video without permission.…
iShieldProtect® Video Encryption Software Whenever you upload video content online, you want it to get viewed. However, what if your content is a premium course like some lecture or a training course? In this case, would you not want unauthorized…
No teacher, trainer, institute, or creator would ever want their high-quality course videos to be widely pirated right after their debut. It's devastating to even think of that. However, it is happening not only in your country but in every…
Hackers are spreading premium content from educational websites within their social circles and groups where coworkers or friends may access courses for free, which puts edtech businesses in a precarious position. Numerous educational institutions are always looking for a solution…
Video encryption is a revolutionized way to protect confidential data from being seen or used by unauthorized sources. For example, if you have produced a video, you want others to view it. But if you are providing any premium data…